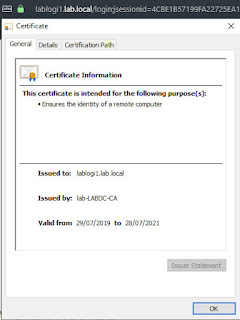
This post will detail how to replace the self signed certificate on the 3 node Log Insight version 4.8 Cluster in my Lab.
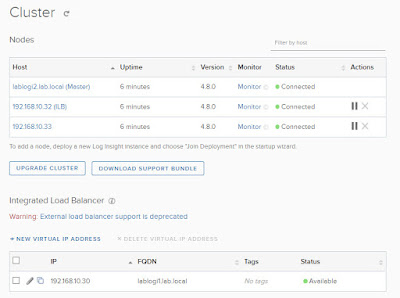
Here is my cluster. I join some of them with an IP but it shouldn’t matter:
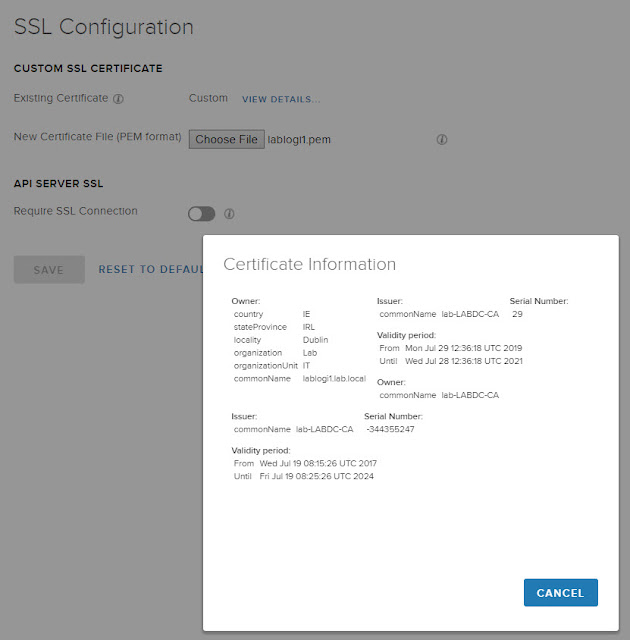
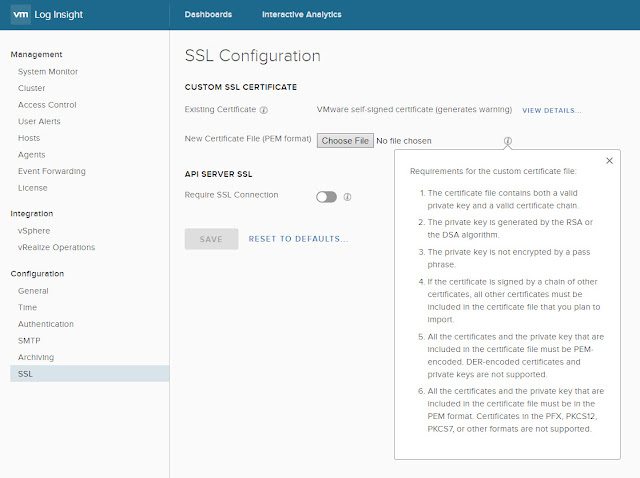
Here is the SSL option under Configuration in the Administration section detailing the PEM requirements. Replacing the cert here has it copied to all nodes (as far as I recall) so it’s a one step process, once you get the PEM certificate correct!
So, I’ve installed OpenSSL on my Domain Controller where my CA is. I need to generate a certificate request in order to sign it. I use OpenSSL to do this, then sign with the Windows CA, then I can export a PEM from that.
The OpenSSL binaries can be installed from here:
https://slproweb.com/products/Win32OpenSSL.html
The file C:OpenSSL-Win64binopenssl.cfg should be backed up and then replaced with the following contents adjusted for your environment:
= sha512
= 2048
= rui.key
= req_distinguished_name
= no
= nombstr
= v3_req
= CA:false
digitalSignature, keyEncipherment, dataEncipherment
= serverAuth, clientAuth
req_distinguished_name ]
= IE
= IRL
= Dublin
= Lab
= IT
= lablogi1.lab.local
You need to replace the values to reflect the FQDN and IPs you are using plus the correct owner details. Yes you need the IP to be listed twice, once as a DNS entry and again as an IP entry!
Now I can execute the command below in the C:OpenSSL-Win64bin directory and generate a CSR / Certificate Request File.
req -new -nodes -out C:OpenSSL-Win64binlablogi1.lab.local.csr -newkey
rsa:2048 -keyout C:OpenSSL-Win64binlablogi1.lab.local.key -config
C:OpenSSL-Win64binopenssl.cfg
I’ve now got two new files, a .key file and the CSR. We’ll open the CSR file and use it to generate a certificate from the CA. Browse to the CA web server http://localhost/certsrv if you’re on the CA itself.
Click Request a Certificate
Click Advanced Certificate Request….
Click Submit a Certificate…..
Paste the CSR contents and choose the Web Server template