Similar Posts
vSphere 7 Ate my HBA
My whitebox uses a Supermicro Motherboard that has an Intel c612 chipset for it’s SATA controllers….
NSX Multitenancy – Part 6 – Integration with NSX Advanced Load Balancer
Welcome to the final part of the blog series on NSX multitenancy. In this article, we…
vRealize Automation Service Broker and Catalog Management – Part 2
In the previous post we covered how a Cloud Template is released and used as a…
100 Most Cited Domains in Google’s AI Mode
Article Performance Data from Ahrefs Linking websites The number of websites linking to this post. Get…
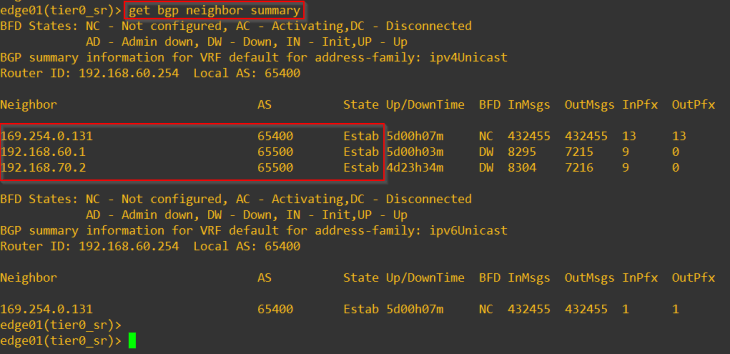
Building an NSX-T Bring Your Own Topology (BYOT) for VMware Enterprise PKS – Part 3
This is Part 3 of the 4-part blog series on ‘Building an NSX-T Bring Your Own…
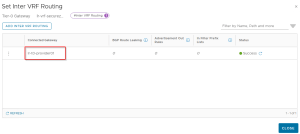
vSphere Supervisor Networking with NSX and AVI – Part 7 – vSphere Namespace with Dedicated T0 VRF Gateway
Welcome to Part 7 of the blog series on vSphere supervisor networking with NSX and AVI….